While going down the Google antitrust rabbit hole for our last article about Jedi Blue, we came across some other cases mentioned in the report that are concerning, to say the least.
It turns out that Big tech’s attacks on our privacy are worse than expected.
In this article, we are shedding light on two more cases that give us another glimpse of what is going on behind the curtains, and we’re providing a few tips on how you can make sure to protect yourself.
Disclaimer: This article is based on the content of a recent anti-trust filing in the United States. Some of the paragraphs mention documents and actions that are not available to the public and hence not verifiable to us.
If you want to read the entire document for yourself, you can find it here:
The violation of 750+ million android users’ privacy
Around October 2015, Google-Android users were presented with the option to back up their WhatsApp messaging history, photos, video, and audio files to Google Drive.
Whatsapp, which is owned by Google’s ‘competitor’ Facebook, stated at the time that chats and calls were end-to-end encrypted: no third parties could not read or listen to them.
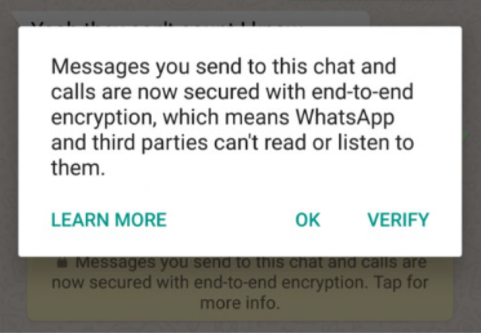
But guess what…
Google had access to private Whatsapp content
According to the antitrust filing, Google wrote in a June 2016 memo, that “when WhatsApp media files are shared with 3rd parties such as Drive, the files are no longer encrypted by WhatsApp.” It goes on to say that “For clarity, all of the [WhatsApp] data stored in Drive is currently encrypted with Google holding the keys.” (164)
This means that Google, as a third party, could in fact access the photos, videos, and audio files that users thought they had shared privately on WhatsApp.

Whatsapp left their user’s data for the taking. Whether Facebook was unaware of the situation or was knowingly giving third parties access to their users’ private data is unclear. However, if the document can be believed, Google knew about this technical vulnerability and went along with it instead of calling for rectification. They had no problem violating millions of users’ privacy.
Hear no evil, see no evil, speak no evil🙉🙈🙊
Google failed to mention the fact that they had full access to this data. The information didn’t appear on the Google Drive website, the Google Drive mobile application, and not even in the Google Drive Terms and Privacy policy. (167)
Why would Google mislead its users and not expose Whatsapp, a competitor-owned company, right away?

Well, by May 2017 they had gained, according to the filing, a staggering 750 million new Whatsapp backup accounts. (169)
Google knew people would refrain from backing up their files if they realized that the company could access their private files, so they decided to keep quiet for their own benefit.
How ironic that they changed their slogan from “don’t be evil” to “do the right thing”, yet fail to live up to either of them.
Google secretly met with competitors to “discuss competition”
Deliberately ignoring privacy breaches is already bad enough, but there’s more.
Paragraphs 170-175 also caught our particular interest: The antitrust filing states that Facebook, Apple, Microsoft, and Google discussed how to forestall consumer privacy efforts, during a meeting in August 2019.
The filing quotes a document from July 31, 2019, that was prepared in advance of this meeting: “We (Google) have been successful in slowing down and delaying the [ePrivacy Regulation] process and have been working behind the scenes hand in hand with the other companies.”

This statement puts an entirely different light on the situation at hand. This goes beyond Google stalling users’ privacy by staying passive. According to the filing, Google is actively taking steps to undermine the advancement of privacy regulations and refer to the destruction of said privacy as a success.
The same obviously goes for Facebook, Apple, and Microsoft.
They didn’t even stop at children
According to paragraph 171 of the document, Google was looking to actively forestall and diminish child privacy protections. The filing quotes that Google planned a meeting with other Big Tech firms to “find areas of alignment and narrow gaps in our positions and priorities on child privacy and safety.” The document even indicates that Google “expressed particular concern” about Microsoft taking child privacy more seriously than Google.

Using the ignorance of adults against them is one thing. Undermining policies for child privacy and safety, however, is on another level of maliciousness. Facebook, Microsoft, and Apple are accomplices and according to the antitrust filing, Google seems to be the tip of the spear. They actively pressured other companies into adopting their shady approaches.
In the document, Google even states that Microsoft’s privacy measures are “subtle privacy attacks” against Google and their “industry colleagues”.
Yes, you read that right. Google describes Microsoft’s measures to provide better user privacy are a “subtle attack”. (174)
How to protect yourself
The more we looked into the antitrust filing, the thinner the ice seemed to get for Google and their co-conspirators. This is especially concerning if we assume this to be the entrance of a much deeper rabbit hole. While these companies are making huge efforts to keep up a public image of caring about privacy, they are actively coordinating and lobbying against user interests.

We would love to see some real, thought-through consequences after the completion of the antitrust filing. In the meantime, all we can do is try to take control of our privacy and data. Some easy to implement steps in doing so are:
Check Privacy settings
Set clear boundaries on what platforms are allowed to do with your information. Try to be aware of the settings and adjust them to your liking.
Share as little information as possible
Try to limit the information you give away to the absolute minimum. Websites and platforms always try to gather as many details about you as possible. Even though this is totally unnecessary, it became common practice and people no longer question this alarming behavior. Fill out the required forms and ignore everything else.
Don’t just blindly “accept the cookies”
Be careful which cookies you accept when visiting a new website. Many websites nowadays offer cookie customization options or a “Reject all” button. We recommend always clicking “Reject all” when you’re visiting a new website for the first time or through a search result.
Be careful what you share online
The more information, pictures, and videos you share the more information of you exist in the depths of the internet. Always ask yourself if the content you share is meant to be published for the rest of your life (especially when you’re interacting with Blockchain technology 😅).
Use VPNs
Using VPNs is an effective way to surf the web anonymously. They hinder third parties to track your browsing activities or locating your machine. If you are unfamiliar with the concept of VPNs you should definitely look into this matter asap.
Spread your identity
With all the privacy and security issues these days, it is hard to directly recommend companies that offer alternatives to the big tech products. One tip from us: Spread your information and online identity over as many different platforms as possible. Today Google offers services for literally every problem or topic in your life. BUT there are smaller alternatives for each of those services. Try to not give one company all your information – spread it out, so that no one has a crystal clear image of you.
– Maps ➡️ OpenStreetMap, OsmAnd
– Search ➡️ DuckDuckGo, Bing
– Storage ➡️ Tresorit, Nordlocker
– E-mails ➡️ ProtonMail, Tutanota
– Browser ➡️ Brave, Opera
– Translate ➡️ Deepl, Linguee
– Messenger ➡️ Signal, Wire
– Online Docs ➡️ CryptPad, Etherpad
– Authenticator ➡️ Authy, FreeOTP
Pay cash and refuse to use member or bonus cards
The hunt for information is not limited to the internet. Payback, member, and bonus cards are the cookies and data collection of the offline world. If privacy is important to you, refuse these cards even if they offer monetary compensation. Companies using these methods are not rewarding you for being a loyal customer but they’re “stealing” your data.